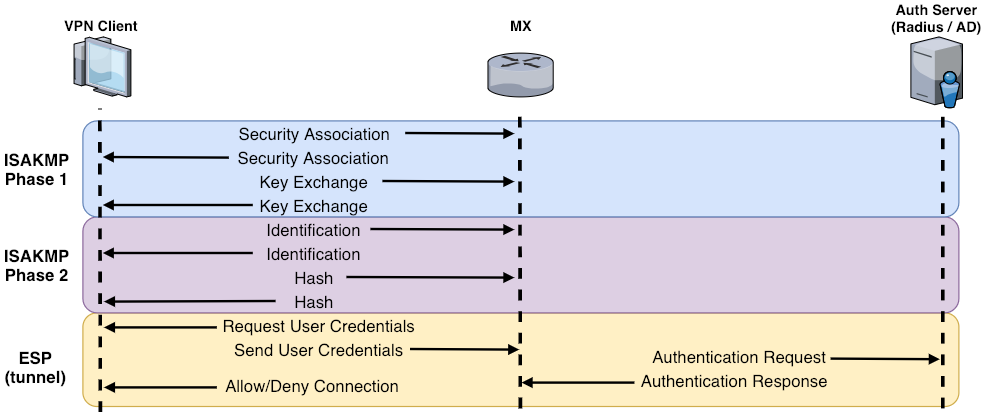
- The VPN: The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
- Re: Cisco Meraki MX84 - trouble with Client VPN setup under this there are 8 rules I'm guessing one of those is for udp/500 or udp/4500, which is needed for client VPN.
- AnyConnect requires a VPN client to be installed on a client device. The AnyConnect client for Windows, MacOS, and Linux are available on the Client Connection section of the AnyConnect configuration page on the dashboard and can be downloaded by a Meraki dashboard administrator.
In the episode 4, I set up a Client VPN on the MX64 Security Appliance!Please Like the video if you liked it, Share it you think others might like it too.
For additional information, refer to the AnyConnect configuration guide.
Client Download
Unlike the ASA, the MX does not support web deploy or web launch, a feature that allows end users to access a web page on the AnyConnect server to download the AnyConnect client. With the MX, there are download links to the client software on the AnyConnect settings page on the dashboard, however, the download links are only available to the Meraki dashboard admin and not the end user. We do not recommend sharing the down link with users as the link expires after every five minutes of loading the AnyConnect settings page.

We recommend downloading the AnyConnect client directly from Cisco.com as there may be an updated version in the Cisco repository. Refer to the doc for the AnyConnect clientrelease notes. We also recommend using either Meraki Systems Manager, an equivalent MDM solution, or Active Directory to seamlessly push the AnyConnect software client to the end user's device.
AnyConnect requires a VPN client to be installed on a client device. The AnyConnect client for Windows, MacOS, and Linux are available on the Client Connection section of the AnyConnect configuration page on the dashboard and can be downloaded by a Meraki dashboard administrator. Please note, the download links on the Meraki dashboard expire after five minutes. The AnyConnect client for mobile devices can be downloaded via the respective mobile stores. You can also download other versions (must be version 4.8 or higher) of the AnyConnect client from Cisco.com if you have an existing AnyConnect license. AnyConnect web deploy is not supported on the MX at this time.
- Installing the AnyConnect client
- You only need the VPN box checked. Once the client has been installed on the device, open the AnyConnect application and specify the hostname or IP address of the MX (AnyConnect server) you need to connect to.
AnyConnect Profiles
An AnyConnect profile is a crucial piece for ensuring easy configuration of the AnyConnect client software, once installed. The MX does not support the use of custom hostnames for certificates (e.g. vpn.xyz.com). The MX only supports use of the Meraki DDNS hostname for auto-enrollment and use on the MX. With the Meraki DDNS hostname (e.g. mx450-xyuhsygsvge.dynamic-m.com) not as simply as a custom hostname, the need for AnyConnect profiles cannot be overemphasized. Profiles can be used to create hostname aliases, thereby masking the Meraki DDNS with a friendly name for the end user.
Cisco AnyConnect client features are enabled in AnyConnect profiles. These profiles can contain configuration settings like server list, backup server list, authentication time out, etc., for client VPN functionality, in addition to other optional client modules like Network Access Manager, ISE posture, customer experience feedback, and web security. It is important to note that at this time, the Meraki MX does not support other optional client modules that require AnyConnect head-end support. For more details, see AnyConnect profiles.
When a profile is created, it needs to get pushed to the end user's device. There are three ways to do this.
1. Through the AnyConnect server (MX): If profiles are configured on the dashboard, the MX will push the configured profile to the user's device after successful authentication.
2. Through an MDM solution: Systems Manager, an equivalent MDM solution, or Active Directory can be used push files to specific destinations on the end user's device. Profiles can also be pushed to the following paths:
Windows
%ProgramData%CiscoCisco AnyConnect Secure Mobility ClientProfile
Mac OS X
/opt/cisco/anyconnect/profile
Linux
/opt/cisco/anyconnect/profile
3. Manually: Profiles can also be preloaded manually to the same paths as listed above.
How to Create a Profile
Profiles can be created using the AnyConnect profile editor. The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on cisco.com. Refer to this link for more details on AnyConnect profiles.
Using the profile editor: The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on Cisco.com. The profile editor only runs on Windows operating systems. The screenshot below shows a configured server ton the Server List Entry option.
When configuration is complete, save the profile. It is recommended to use a unique file name to avoid profile overrides by other AnyConnect servers, then you can upload the file to the profile update section on the AnyConnect settings page.
Please note that only VPN profiles are supported on the MX at this time. This means you cannot push NVM, NAM, or Umbrella profiles via the MX.
- Select enable profiles, upload your xml file, and save your configuration
- After a user successfully authenticates, the configured profile gets pushed to the user's device automatically
- The result of the .xml can be seen below, after successful authentication to the AnyConnect server; this gives users the ease of selecting VPN servers on the AnyConnect client
The Meraki DDNS hostname is not easy to remember, therefore end users are not expected to use it directly. Profiles should be used to make connecting to the AnyConnect server easy for end users.
The VPN:
The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
The Encryption Method:
Along with the L2TP/IP protocol the Meraki client VPN employs the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase 2. Best practice dictated that the shared secret should not contain special characters at the beginning or end.
Enabling Client VPN:
Select Enabled from the Client VPN server pull-down menu on the Security Appliance -> Configure -> Client VPN page. You can then configure the following options:
- Client VPN Subnet: The subnet that will be used for Client VPN connections. This should be a private subnet that is not in use anywhere else in your network. The MX will be the default gatway on this subnet and will route traffic to and from this subnet.
- DNS Nameservers: The servers VPN Clients will use to resolve DNS hostnames. You can choose from Google Public DNS, OpenDNS, or specifying custom DNS servers by IP address.
- WINS: If you want your VPN clients to use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
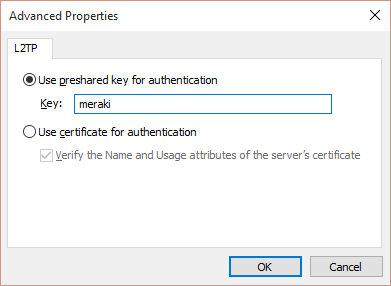
- Secret: The shared secret that will be used to establish the Client VPN connection.
- Authentication: How VPN Clients will be authenticated.
- Systems Manager Sentry VPN Security: Configuration settings for whether devices enrolled in systems manager should receive a configuration to connect to the Client VPN.
Authentication:
The VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your authentication method.
Meraki Cloud Authentication:
Use this option if you do not have an Active Directory or RADIUS server, or if you wish to manager your VPN users via the Meraki cloud. To add or remove users, the User Management section at the bottom of the page. Add a user by selecting “Add new user” and entering the following information:
- Name: Enter the user’s name
- Email: Enter the user’s email address
- Password: Enter a password for the user or select “Generate” to automatically generate a password
- Authorized: Select whether this user is authorized to use the Client VPN
In order to edit an existing user, click on the user under User Management section. To delete a user, click the X next to the user on the right side of the user list. When using Meraki hosted authentication, the user’s email address is the username that is used for authentication.
RADIUS:
Use this option to authenticate users on a RADIUS server. Click Add a RADIUSserver to configure the server(s) to use. You will need to enter the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.

Active Directory:
Use this option if you want to authenticate your users with Active Directory domain credentials. You will need to provide the following information:
- Short Domain: The short name of your Active Directory domain.
- Server IP: The IP address of an Active Directory server on the MX LAN.
- Domain Admin: The domain administrator account the MX should use to query the server.
- Password: Password for the domain administrator account.
For example, considering the following scenario: You wish to authenticate users in the domain test.company.com using an Active Directory server with IP 172.16.1.10. Users normally log into the domain using the format ‘test/username’ and you have created a domain administrator account with the username ‘vpnadmin’ and the password ‘vpnpassword’.
- The Short domain would be ‘test’.
- The Server IP would be 172.16.1.10
- The Domain admin would be ‘vpnadmin’
- The Password would be ‘vpnpassword’.
At this time, the MX does not support mapping group policies via Active Directory for users connecting through the Client VPN.
Cisco Meraki Client Vpn Split Tunnel
Systems Manager Sentry VPN Security:
When using Meraki cloud authentication, Systems Manager Sentry VPN security can be configured. If your Dashboard organization contains one or more MDM networks. Systems Manager Sentry VPN security allows for your devices enrolled in Systems Manager to receive the configuration to connect to the Client VPN through the Systems Manager profile on the device.
Cisco Meraki Vpn Client Windows 10
To enable Systems Manager Sentry VPN security, choose Enabled from the Client VPN server pulldown menu on the Security Appliance -> Configure -> Client VPN page. You can configure the following options:
Cisco Meraki Windows 10 Vpn
- Install Scope: The install scope allows you to select a set of Systems Manager tags for a particular MDM network. Devices with these tags applied in a Systems Manager network will receive a configuration to connect to this network’s Client VPN server through their Systems Manager profile.
- Send All Traffic: Select whether all client traffic should be sent to the MX.
- Proxy: Whether a proxy should be used for this VPN connection. This can be set to automatic, manual, or disabled.
 Note:
Note:When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud. Usernames are generated based on a hash of unique identifier on the device and the username of that device. Passwords are randomly generated.
Meraki Vpn Setup Windows 10
Was this article helpful?
Meraki Vpn Client Install
Related Articles
