- Does Mackeeper Actually Work
- Kromtech Mackeeper Account
- Mackeeper Software
- Reviews Of Mackeeper Software
- Kromtech Mackeeper
The makers of MacKeeper — a much-maligned software utility many consider to be little more than scareware that targets Mac users — have acknowledged a breach that exposed the usernames, passwords and other information on more than 13 million customers and, er…users. Perhaps more interestingly, the guy who found and reported the breach doesn’t even own a Mac, and discovered the data trove merely by browsing Shodan — a specialized search engine that looks for and indexes virtually anything that gets connected to the Internet.
IT helpdesk guy by day and security researcher by night, 31-year-old Chris Vickery said he unearthed the 21 gb trove of MacKeeper user data after spending a few bored moments searching for database servers that require no authentication and are open to external connections.
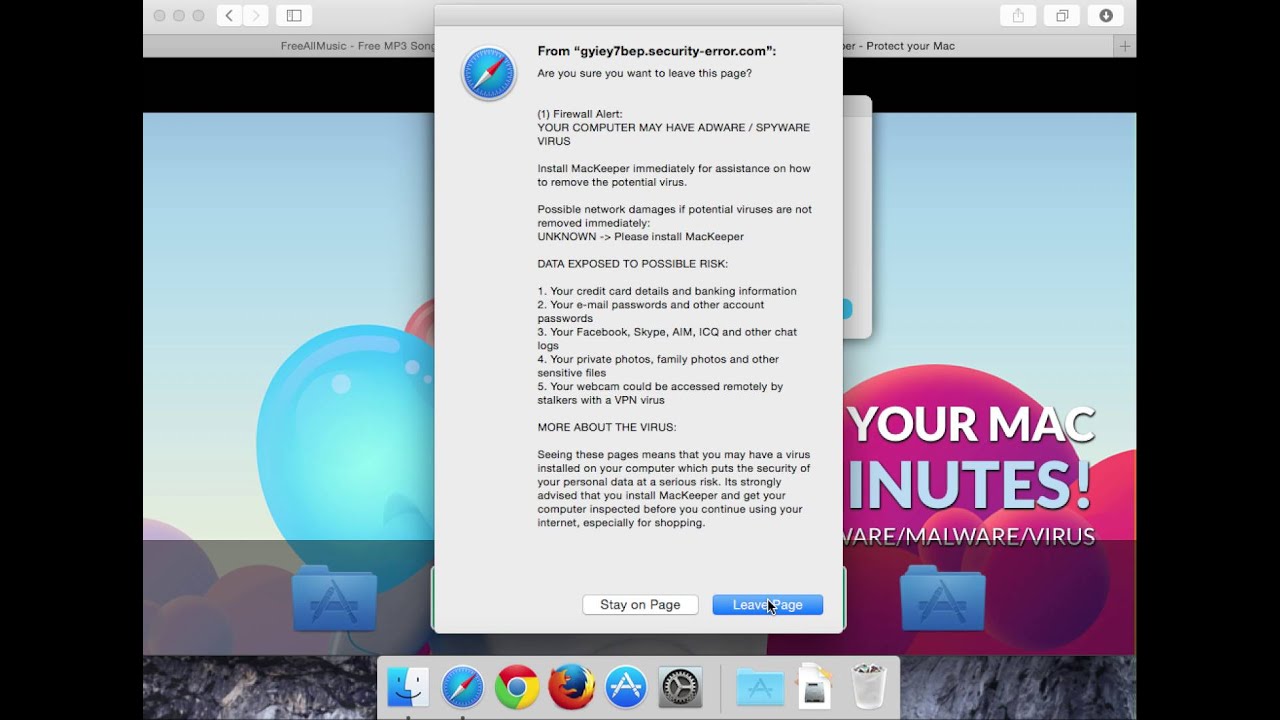
Kromtech.com is a shady website, which is known to spread the ad-supported app MacKeeper. That’s how this malicious software got the name Kromtech MacKeeper. The appearance of Kromtech.com means that you most likely have unwanted software installed on your computer, which makes your browser to constantly load the unreliable page. If you've had a Mac for a while, there's a good chance you've come across an ad for a software called Mackeeper. It's a Cleaning utility originally developed by Zeobit LLC which was acquired by Kromtech Alliance Corp, a German-based IT investment and development company, in 2015. MacKeeper has been launched in 2010 by ZeoBIT, LLC. In 2013, the software was sold to Kromtech Alliance Corp. The previous company, ZeoBIT, used aggressive marketing strategies to promote the software, which consequently earned a bad reputation for the product.
Vickery told Shodan to find all known instances of database servers listening for incoming connections on port 27017. “Ports” are like doorways that govern access into and out of specific areas of a server, and each port number generally maps to one or a handful of known Web applications and services. Port 27017 happens to be associated with MongoDB, a popular database management system.
In short order, Vickery’s request turned up four different Internet addresses, all of which he later learned belonged to Kromtech, the company that makes MacKeeper.
“There are a lot of interesting, educating and intriguing things that you can find on Shodan,” Vickery said. “But there’s a lot of stuff that should definitely not be out there, and when I come across those I try to notify the owner of the affected database.”
Vickery said he reached out the company, which responded quickly by shuttering public access to its user database, and publicly thanking him for reporting it.
“Some 13 million customer records leaked from is aware of a potential vulnerability in access to our data storage system and we are grateful to the security researcher Chris Vickery who identified this issue without disclosing any technical details for public use,” the company said in a statement published to its site totday. “We fixed this error within hours of the discovery. Analysis of our data storage system shows only one individual gained access performed by the security researcher himself. We have been in communication with Chris and he has not shared or used the data inappropriately.”
Kromtech said all customer credit card and payment information is processed by a 3rd party merchant and was never at risk.

“Billing information is not transmitted or stored on any of our servers. We do not collect any sensitive personal information of our customers,” the statement continues. “The only customer information we retain are name, products ordered, license information, public ip address and their user credentials such as product specific usernames, password hashes for the customer’s web admin account where they can manage subscriptions, support, and product licenses.”
Vickery said Kromtech told him its database had been inadvertently exposed as a result of a server misconfiguration that was introduced just last week. But Vickery said he doubts that’s the case, because some of the Shodan records he found that pointed back to Kromtech’s database were dated mid-November 2015.
“The funny thing is, I don’t even own a Mac, and I had never heard of MacKeeper until last night,” Vickery said. “I didn’t know it was some sort of scamming scareware or software that pushes itself on people. The irony here is pretty thick.”
Vickery said he was able to connect to the database that Shodan turned up for him just by cutting and pasting the information into a commercial tool built to browse Mongo databases. Asked whether he’s worried that some clueless organization or overzealous prosecutor might come after him for computer hacking, Vickery said he’s not concerned (for background, see the controversy over bone-headed cases brought against researchers under the Computer Fraud and Abuse Act).
“It’s a concern, but I’ve made peace with that and you can’t live your life in fear,” he said. “I feel pretty confident that if you configure a server for public access — without authentication — and it gets publicly accessed, that’s not a crime.”
I admire Vickery’s courage and straightforward approach, and his story is a good reminder about the importance of organizations using all of the resources available to them to find instances of public access to sensitive or proprietary data that shouldn’t be public. Consider taking the time to learn how to use Shodan (it’s actually fairly intuitive, but some data may only be available to paying subscribers); use it to see if your organization has unnecessarily exposed databases, networking devices, security cameras and other “Internet of Things” devices.
Finally, if you’re a MacKeeper customer and you re-used your MacKeeper user password at other sites, it’s now time change that password at the other sites — and not just to your new MacKeeper password! For more password do’s and don’ts, check out this primer.
SPECIAL OFFER
Offer for Mac victims, affected by MacKeeper (Kromtech) Virus.The MacKeeper (Kromtech) Virus threat could come back on your Mac several times if you do not manage to detect and remove its hidden files and main objects. We suggest that you download SpyHunter for Mac as it will scan for all types of malicious objects, installed with it. Removal with SpyHunter can happen quickly and may save you hours in trying to uninstall MacKeeper (Kromtech) Virus by yourself.
Further information on SpyHunter for Mac. Before proceeding, please see SpyHunter for Mac EULA and Privacy Policy. Bear in mind that SpyHunter for Mac scanner is completely free. If the software detects a virus, you can also remove threats by purchasing SpyHunter’s full version.
Another way by which you may detect if you are about to have adware on your computer is to catch it while being installed. Programs like MacKeeper (Kromtech) Virus are usually being spread via third-party programs. The third-party software’s installers can be with included programs that are advertised as free bonus software or other seemingly useful code. However, the Search Mine Mac threat can present a potential harm to your computer and this is why experts often recommend to remove programs like it immediately.
| Threat Name | MacKeeper (Kromtech) Virus |
| Category | Trojan Horse/Hijacker. |
| Main Activity | Slithers onto your Mac and may steal information from it. A heuristic detection for most conventional Trojan horses. |
| Signs of Presence | Slow PC, changed settings, error messages, suspicious PC behaviour. Logins from unknown sources on your online accounts. |
| Spread | Via malicious e-mail spam and set of infection tools. |
| Detection+Removal | Note!For Mac users, please use the following instructions. |
What Harm Can MacKeeper (Kromtech) Virus Trojan Do to My Mac?
In this digital age, Virus apps can be very significant not only to your Mac, but to you as well. Since most users keep their important files on Macs, all of their crucial information becomes at risk. This means that your personal ID number or other financial data that you may have used on a Mac infected by MacKeeper (Kromtech) Virus virus can be compromised and used for malicious purposes. This is the primary reason why this threat should be dealt with immediately.
Does Mackeeper Actually Work
The reason why viruses, like the MacKeeper (Kromtech) Virus threat are a significant menace, is that it has multiple different malicious functions that are utilised on your Mac. The features of a virus may vary, depending on what type it is, but it is safe to assume that the MacKeeper (Kromtech) Virus virus can do the following on your PC:
- Steal the passwords from the Macr and obtain the keystrokes from it via Keyloggers.
- Destroy data on your Mac, like delete files. This may even result in damaging your Mac OS.
- Remotely monitor your activity. This means that whatever you do and see on your screen, the hacker who infected you can also see.
- Disable your Windows operating system via a DDoS attack (Denial of Service).
- Use your Mac’s resources (CPU and Video Card) to mine cryptocurrencies, like BitCoin.
- Harvest system data and login information automatically from your web browsers.
- Install other viruses on your Mac which may cause even more damage.
- Display fake tech support screens that can lure you into a scam.
The primary method which you can use to detect a Trojan is to analyse hidden processes on your Mac This is achievable by downloading process monitoring apps, like Process Explorer. However, you will have to have a trained eye on how to detect the malicious processes and how to remove those without damaging your Mac. This is why, as a swift solution, a Mac-specific removal tool should be used, according to security experts. Such removal software will automatically scan for viruses like MacKeeper (Kromtech) Virus and other suspicious apps and get rid of them quickly and safely while protecting your Mac against threats in the future.
Note!MacKeeper (Kromtech) Virus could remain on your Mac if you are not careful during removal. We recommend that you download and run a scan with Combo Cleaner now to professionally clean up your Mac in now just in 5 minutes..
Preparation Before Removing MacKeeper (Kromtech) Virus
1.Make sure to backup your files.
2.Make sure to have this instructions page always open so that you can follow the steps.
3.Be patient as the removal may take some time.
Step 1: Uninstall MacKeeper (Kromtech) Virus from Your Mac:
Kromtech Mackeeper Account
Mackeeper Software

Step 2: Remove MacKeeper (Kromtech) Virus from Your Web Browsers.
1. Remove any MacKeeper (Kromtech) Virus presence from Google Chrome.- Open Chrome and click on the drop-down menu at the top-right corner.
- From the menu open “Tools” and click on “Extensions”.
- Find any MacKeeper (Kromtech) Virus – related add-ons and extensions and click on the garbage icon to remove them.
- Open Firefox and select the top-right menu.
- From it, click on “Add-ons” setting.
- Click on the suspicious extension and click “Remove”.
- Restart Firefox.
- Start Safari.
- Click on the Safari drop-down menu on top-right.
- From the drop-down menu, click Preferences.
- Click on “Uninstall” and accept any prompts.
Reviews Of Mackeeper Software
Step 3:Run a free scan now to remove MacKeeper (Kromtech) Virus files and objects from your Mac.
According to security professionals, the best way to effectively secure your Mac against threats such as MacKeeper (Kromtech) Virus is to scan it with an advanced cleaner software. Combo Cleaner has the professional capabilities of detecting all threats and remove them from your Mac safe and fast.
Kromtech Mackeeper
