The Secure Shell (SSH) protocol provides a remote login similar to Telnet, except that it uses more secure network services. SSH provides stronger password authentication than Telnet and uses. In this lab scenario you will learn to configure SSH on four routers connect together via Frame-Relay.
The SSH client sends a packet to the server and hangs for 10 seconds (send packet: type 50) The server response arrives and everything proceeds normally (receive packet: type 51) So, we are waiting for 10 seconds for the server to get back to us with some kind of response (after successfully establishing a TCP connection). SSH (Secure Shell) is one of the most used protocols in network World. As a secured alternative of Telnet, SSH is always in the life of a network engineer. It helps us to connect our routers, swithces and any other network equipments. Especially because of SSH is more secure, it.
Secure Shell (SSH) is a replacement for older remote shell programs such as telnet. SSH uses encryption to protect the contents (most notably passwords) being sent over its connection.
History
XXX - add a brief description of SSH history
Protocol dependencies
TCP: Typically, SSH uses TCP as its transport protocol. The well known TCP port for SSH traffic is 22.
Example traffic
XXX - Add example traffic here (as plain text or Wireshark screenshot).
Wireshark
The SSH dissector in Wireshark is functional, dissecting most of the connection setup packets which are not encrypted.
Unlike the TLS dissector, no code has been written to decrypt encrypted SSH packets/payload (yet). This is also not possible unless the shared secret (from the Diffie-Hellman key exchange) is extracted from the SSH server or client (see, as an example of a mechanism to extract internal information of that sort, the 'SSLKEYLOGFILE' method in TLS). Work on SSH2 decryption is tracked at https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=16054
Preference Settings
Packet Tracer Configure Ssh
The SSH dissector has a preference to determine whether it should reassemble PDUs spread across multiple TCP segments. For this to work the TCP option 'Allow subdissectors to reassemble TCP streams' must be enabled.
Example capture file
Ssh Packet 50
XXX - Add a simple example capture file to the SampleCaptures page and link from here. Keep it short, it's also a good idea to gzip it to make it even smaller, as Wireshark can open gzipped files automatically.
Display Filter
A complete list of SSH display filter fields can be found in the display filter reference
Show only the SSH based traffic:
Capture Filter
You cannot directly filter SSH protocols while capturing. However, if you know the TCP port used (see above), you can filter on that one.
External links
RFC 4250 - The Secure Shell (SSH) Protocol Assigned Numbers
RFC 4251 - The Secure Shell (SSH) Protocol Architecture
Vag com 409.1 driver for mac. RFC 4252 - The Secure Shell (SSH) Authentication Protocol
RFC 4253 - The Secure Shell (SSH) Transport Layer Protocol
RFC 4254 - The Secure Shell (SSH) Connection Protocol
RFC 4419 - Diffie-Hellman Group Exchange for the Secure Shell (SSH) Transport Layer Protocol
RFC 5656 - Elliptic Curve Algorithm Integration in the Secure Shell Transport Layer
Other documents from the concluded Secure Shell (secsh) IETF working group
IANA: Secure Shell (SSH) Protocol Parameters
Discussion
- 1 minPacket Tracer 1.3.6 Configure Ssh
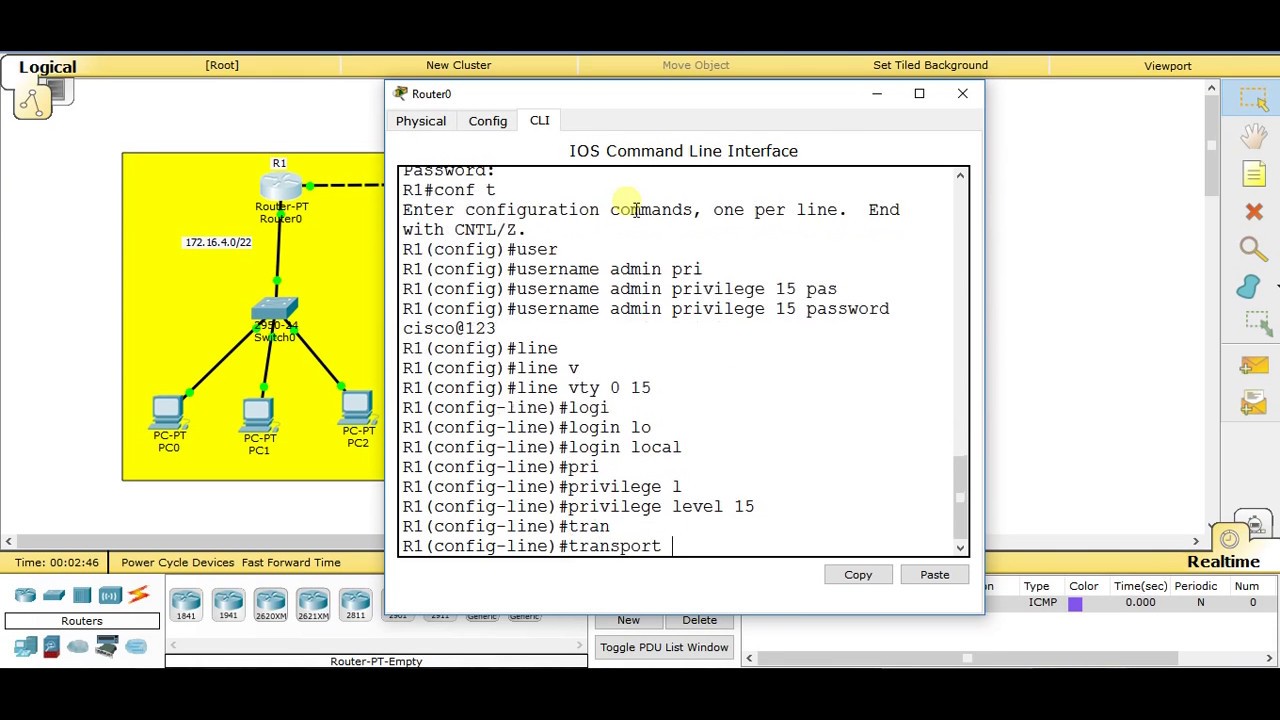
To enable telnet or SSH on Cisco router, simply do it with “line vty” command. lets Configure:
First create topology Network. and set a static IP for PC client, router and switch. See the picture below.
Ssh Packet Too Long
Go to Router0 console and configure Hostname, Secret password and telnet with “line vty” command.
- “Enable secret ‘your password’” command for your router password user privileges.
- The “line vty” command enable the telnet and the “0″ is just let a single line or session to the router. If you need more session simultaneously, you must type “line vty 0 10“, its mean 11 client can access telnet.
- The “logging synchronous” command stops any message output from splitting your typing.
The “exec-timeout” command just sets the time-out limit on the line from the default to “10″ minutes.
Testing Telnet Connectivity.
Let’s test telnet from the admin or client PC. Type telnet 192.168.1.1 and press enter, then enter the telnet username & password. Next type enable command and press enter, then type the router password.
Now you are remotely connected to router R1 and you can execute all router commands through telnet command line interface.
SSH Configuration.
- “line vte 1 3” <~ this command will set only line 1 to 3 Virtual Teminal Lines can access SSH.
- “username budi password luhur” <~ this your username and password for SSH access.
- “crypto key generate rsa” command, when ask you “How many bits in the modulus [512]:” just type “1024″ and press enter. The system will generate 1024 bits keys to secure session lines. You can choose modulus in the range of 360 to 2048.
service password-encryption <~ encrypt your SSH password.
Testing SSH Connectivity
From a client PC, open the command line and type “ssh -l budi 192.168.1.1” then press enter.
Now we have connected successfully and the connection is secured with Secure Shell.
Related Posts
